Recently, I was trying to use my previously
automated Nessus Automation scripts and detected they aren’t working on latest
Nessus 5.2 XMLRPC. Last time, I
automated network scanning tasks using XMLRPC in Perl but strange it did not
work anymore with Nessus 5.2.
Here’s the error message I got while
running my old scripts:
Cannot login to: https://localhost:8834/
I tried to resolve this error, read latest
XMLRPC documentation but could not made it working. I then used XMLRPC in
Python and this did not worked
either. Strange!!!
Next and last attempt was to use XMLRPC in
Ruby and this worked for me..:) To make
this working, you need to have nessus-xmlrpc gem installed within your ruby
installation (obviously). Refer here for complete installation of Ruby and gem on Mac.
Here are my Nessus 5.2 working script using ruby XMLRPC:
#!/usr/bin/env ruby
require 'nessus-xmlrpc'
ARGV.each do|a|
a
= ARGV[1]
n=NessusXMLRPC::NessusXMLRPC.new('','username','password');
if n.logged_in
id,name = n.policy_get_first
puts "using policy ID: " + id + " with name: " +
name
uid=n.scan_new(id,"#{ARGV[0]}","#{ARGV[0]}")
puts "scanning for: " + "#{ARGV[0]}"
puts "report will be saved as " + "#{a}_report.xml"
puts "status: " + n.scan_status(uid)
while not n.scan_finished(uid)
sleep 10
end
content=n.report_file_download(uid)
File.open("#{a}_report.xml", 'w') {|f| f.write(content) }
end
end
Above script takes two user input from
standard STDIN i.e. IP Address and Report Name using a shell script. Here’s is
my shell script that I use to run Nessus against a single IP:
#! /bin/sh
echo "Enter the IP address to
scan:"
read ipaddr
echo "Enter the report name:"
read filename
echo "Nessus running for $ipaddr"
ruby nessus.rb $ipaddr $filename
echo "Completed scans for IP:
$ipaddr"
echo "Output saved starting with
$filename"
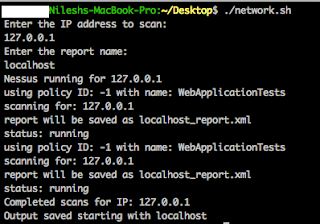
Just copy above scripts and place them in
same folder and you are ready to go from terminal. Here’s a sample output for
your reference:
Cheers!!!